It’s Cybersecurity Awareness Month!
Welcome to the final post in this three-part series. We’re doing our part for #BeCyberSmart by focusing on the risk management aspect of cybersecurity all through October. Earlier, we dug into gaining team engagement with cybersecurity risk management, and five cybersecurity mistakes your organization can avoid.
Reading this, you’re obviously aware of and care about cybersecurity risks. We care, too, and work hard to maintain oversight and to identify our shadow IT. We use our own tool to assess and mitigate our cybersecurity risk.
Some cybersecurity risks are easily overlooked and remain hidden. They don’t appear to be directly connected to your business capabilities at first glance. Looking at your physical product development and business capabilities, you may not see a direct connection to a mail server in a data center on the other side of the world. However, you may still suffer if there is a zero-day exploit that affects your suppliers. Other risks, like shadow IT, remain anonymously connected and unknown.
Unfortunately, we can’t always control what’s happening on another continent or what our colleagues download. We can, however, rationalize and assess our own cybersecurity risk. With complete oversight, so that our organization is prepared to deal with unexpected changes that appear to be unrelated.
🛡We’ve found three effective ways to manage that risk, including using crowdsourcing, visualizations, and modeling.
3. Crowdsource Cybersecurity Risk With Surveys and Broadcasts
Some companies manage hundreds or even thousands of applications. Depending on if they have an Enterprise Architecture (EA) team or not, a high number of these applications might be outdated and struggling to align with the enhanced customer-centric processes they are supposed to support. 
An unknown number may be creating shadow IT, with the potential to compromise sensitive data. Even if the EA team successfully upgrades their technology, they face upgrade-related risks that persist after the migration is complete.
Ardoq’s solution to this cybersecurity risk assessor:
- Surveys crowdsource the data collection to users and provide a fast and easy way to gather any kind of data.
- Broadcasts select and send to the correct audience for a survey, and send reminders. Naturally, this includes templates, timed send, and scheduled send functions.
Surveys can indicate where risk will impact the business’s ability to operate effectively. If you’re planning a cloud migration, Surveys identify the teams that need to be involved in the planning process. You can create Surveys for specific users and user groups, and they will only have access to create or update specific areas.
Broadcasts allow you to automate Surveys in addition to setting parameters for the surveys you send. For example, to help calculate risk impact, Surveys can be broadcast to risk team owners to create awareness and capture approvals. From a risk assessment standpoint, they are easily utilized to canvas and alert key risk stakeholders across your entire organization about unmapped applications, applications approaching end-of-life, or out-of-service/support that the business is relying on.
These tools document business realization, updates, and bug fixes, so these applications (and the related business capabilities they support) don’t become easy targets that are vulnerable to hackers and cybercriminals. Managing these issues is essential in application risk management, as outdated or unsupported applications can expose an organization to unforeseen cybersecurity risks.
2. Visualize Risk Management
Once this data is gathered, it needs to be presented in a way that makes sense. If a picture is worth 1,000 words, data visualization is worth 10,000. Ardoq comes with visualization tools that help analyze the results from the surveys you’ve broadcast, without months of work. In addition, using workspaces, you can have governance over how you document and structure your information. With an established workspace, you can create metamodels that show connections through component types and references.
Consider third-party applications which have access to limited amounts of your data. In many companies, it’s simple for employees to download an application onto their computers. The Broadcasts and Surveys help collect information about what applications users are actually using, and a map shows what’s happening where.
Some applications can still be used but are at higher risk. If you have a department or business capability that is relying on riskier tools, visualizing can help you identify where you might run into problems.
Visualization makes identifying the high-risk business areas easier for non-IT employees to understand. Tell them about the risk, and they may not listen, and likely they’ll want to continue using that useful application. However, if you show them a heat map detailing which departments use potentially risky tools, they can see the points where the company could be compromised.
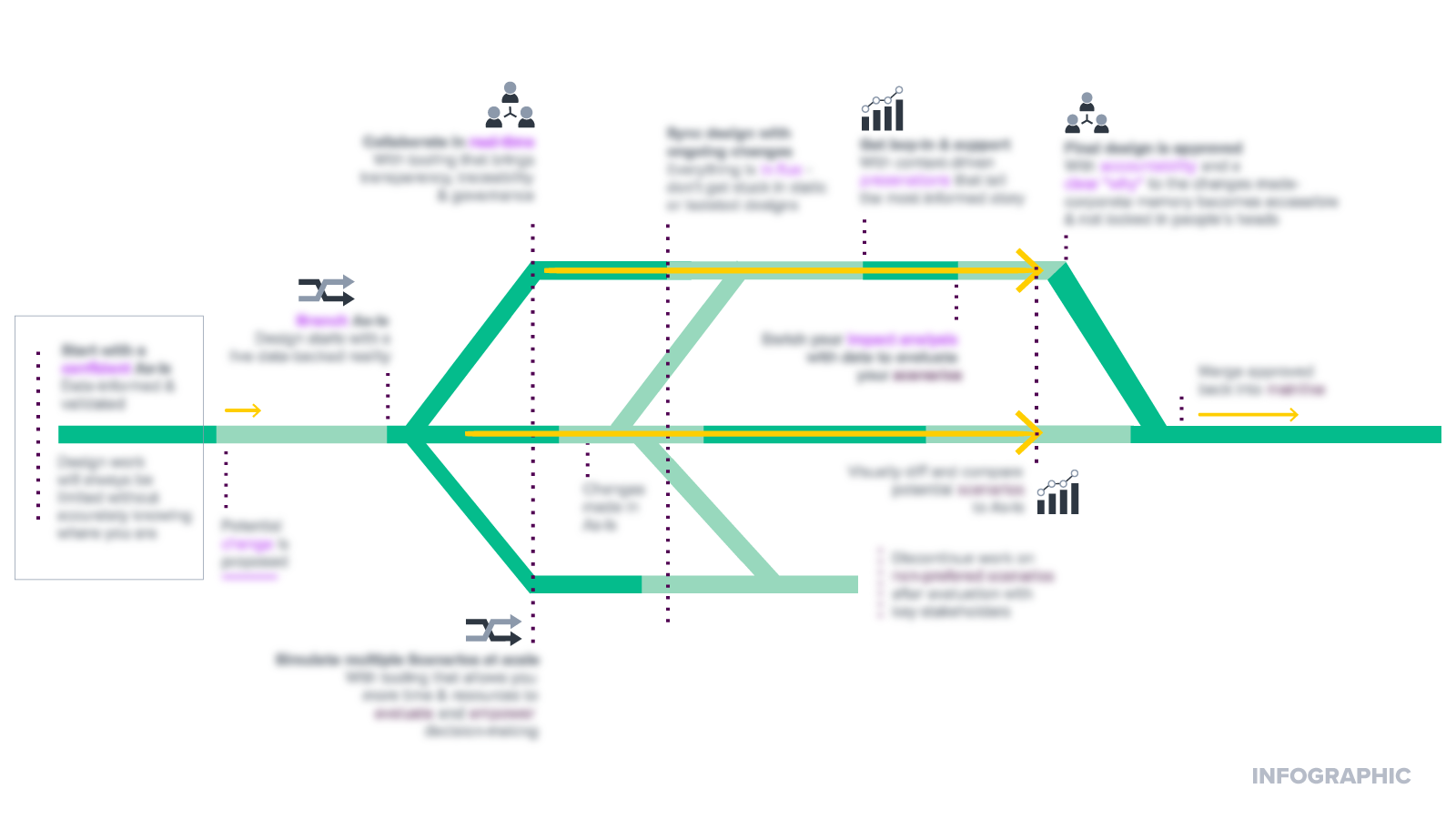
1. Model Scenarios to See the Future
The metamodel allows Ardoq to automatically create visualizations and validate input. A platform feature we find best for cybersecurity includes Scenarios, which helps you play out the consequences of a cyberattack and the fall-out. So instead of running out of products you sell because of vendors, you will know where the supply chain will run short and can have a Plan B ready. With Scenarios, you can select a subset of your components from across your workspaces, where you can make changes in isolation from the mainline. You can then compare, share, and present the suggested changes to your team and other stakeholders to get buy-in and alignment, and to find the best way forward.
Like most of us, many of your critical supply-chain services are probably hosted in the cloud. Let’s consider a hypothetical situation that could affect your business because of this: If your vendor shuts down because of a cyber attack, your supplies might suddenly dwindle. With Scenarios, you could model how this would impact your ability to deliver and which processes fail.
Before making any changes to adapt to this or other roadblocks, we need to understand what potential impact the security designs could have. This is where Ardoq’s key functionality around branching and future state modeling comes into play. Instead of starting from scratch with manual techniques, we can utilize the existing data set maintained in Ardoq to start the security design workflow. In other words, the architect can model against something based on reality.
The benefits of branching are many. Our customers most often report time saved in the modeling phase and increased quality, since you can keep your branch in sync as the changes happen. You can create as many scenarios as needed, which gives you ample opportunity to compare multiple future states. You can even run differential analysis both analytically and visually to understand the trade-offs.
Improve your time-to-decision and quickly determine the impact of proposed scenarios. See which teams will be involved and potential timelines. Avoid spending $10 on a $5 risk. Modeling helps you identify the areas you need to focus on in risk management.
We can’t control when others are hit by a zero-day exploit, but we can be prepared for it. With Ardoq, you can have a better understanding of how breaches in cybersecurity will affect your business.
How We Use Ardoq as a Cybersecurity Risk Assessment Tool:
Everyone can mitigate cybersecurity risk with careful management and by using:
- Visualization tools like Workspace, Metamodels, and Scenarios help us see and map out the possible outcomes of a cyberattack.
- Crowdsourcing helps us have a current up-to-date overview of our application. This is quickly managed with automated Surveys and Broadcasts.
- Timelines and Modeling use existing data, so our model is based on reality.
➡️ Want to discover how you can use Ardoq to identify shadow IT, assess and mitigate cybersecurity risks? 🛡
 Ardoq
This article is written by Ardoq as it has multiple contributors, including subject matter experts.
Ardoq
This article is written by Ardoq as it has multiple contributors, including subject matter experts.