In today's digital landscape, application vulnerabilities are a leading cause of security breaches. The 2024 Verizon Data Breach Investigations Report indicates that 14% of all breaches involved the exploitation of vulnerabilities as an initial access step, nearly tripling from the previous year. This underscores the critical importance of Application Risk Management (ARM) in identifying and mitigating these risks.
This guide explores ARM's key components, integration within Enterprise Architecture, and practical strategies for 2025.
Jump to:
- What Is Application Risk Management (ARM)?
- Why Is Application Risk Management Important in Enterprise Architecture?
- Scope and Rationale: Questions Answered Using Application Risk Management
- Roles and Components of Risk
- What Is an Application Security Risk Assessment?
- Phases of Application Risk Management: The X-Step Guide to Building a Comprehensive Program
- Best Practices for Implementing Application Risk Management in EA
- Application Risk Management Challenges
- Enterprise Application Risk Management with Ardoq: Secure What Matters Most to a Business
- FAQs About Application Risk Management
What Is Application Risk Management (ARM)?
Application Risk Management (ARM) is the systematic process of identifying, assessing, and mitigating application risks to ensure their secure and effective operation.
It involves evaluating potential threats, vulnerabilities, and impacts that could compromise application integrity, confidentiality, and availability.
ARM encompasses various practices, such as security testing, code review, compliance checks, and incident response planning. Effective ARM aims to minimize risks from cyber-attacks, data breaches, and operational failures, ensuring applications meet regulatory requirements and business objectives. It is critical in safeguarding IT infrastructure and maintaining trust in digital systems.
What Are Examples of Application Risk?
With the ever-increasing reliance on IT, an organization can and will face many risks. Mitigation for these risks must be considered and applied to maintain business viability and continuity. Examples of application risks include:
-
Security vulnerabilities that arise from software flaws such as SQL injection, cross-site scripting, and buffer overflows. Attackers can exploit these to gain unauthorized access or disrupt services.
-
Data breaches can occur if inadequate data protection measures are in place. These can potentially expose sensitive information such as personal data, financial records, or intellectual property.
-
Insufficient authentication and authorization controls can allow unauthorized users to gain access or perform actions beyond their permissions.
-
Compliance violations through not adhering to industry regulations and standards, such as DORA, GDPR, HIPAA, or PCI-DSS, can lead to legal penalties and reputational damage.
-
Operational failures, such as software bugs, downtime, or performance bottlenecks, will affect the application's reliability and user experience.
-
Third-party risks arise where there are dependencies on external libraries, APIs, or vendors. These may introduce vulnerabilities or operational risks.
-
Data integrity risks due to application logic flaws can lead to incorrect processing or decision-making.
-
Denial of service attacks results from overwhelming an application with excessive traffic, causing service interruptions and accessibility issues.
Managing these risks is crucial for ensuring application security, functionality, and regulation compliance.
Why Is Enterprise Architecture Important in Application Risk Management?
Enterprise Architecture (EA) performs a crucial role within ARM, with the key impacts being:
-
Providing a holistic view of an organization's IT landscape, including applications, data flows, and infrastructure and existing IT governance measures. This macro perspective helps identify interdependencies and systemic vulnerabilities that might be overlooked when examining isolated applications.
-
Standardization of processes, technologies, and methodologies across the organization helps implement consistent security measures, reducing the risk of inconsistencies and gaps that could be exploited.
-
Alignment with business goals is ensured so that IT initiatives, including risk management efforts, are aligned with business objectives. This alignment helps prioritize risks that could significantly impact business operations and customer trust.
-
EA-generated insights assist with resource optimization, helping optimize the deployment of security measures, and ensuring that critical applications receive appropriate attention and resources to mitigate risks effectively.
-
Regulatory compliance within an EA framework ensures that applications adhere to relevant regulations and standards, thus reducing the risk of legal and financial penalties.
-
Change management, especially structured change management processes, is part of EA and ensures that risks associated with application updates, migrations, and integration are systematically assessed and managed.
-
Data integrity and security, through clear data governance policies, are established by EA, to protect data integrity and ensure secure data flows across applications, reducing the risk of data breaches and loss.
-
Risk communication via a common EA lead, language, and framework allows for risk discussion across different stakeholders, improving communication and facilitating coordinated risk management efforts.
Overall, EA is a strategic tool that enhances ARM's effectiveness, consistency, and efficiency, safeguarding the organization's IT ecosystem and business operations.
The Value of Focusing on Application Risk Management
The primary stakeholders for app risk management are the company roles responsible for its execution. Specifically, these include the COO and CIO, the head of risk and compliance, risk owners and control owners, application owners, and others accountable for applications.
The value to organizations from implementing Application Risk Management includes:
Enhanced Security by identifying and mitigating vulnerabilities, protecting applications from cyber threats and unauthorized access. These reduce the likelihood of breaches and maintain the security of sensitive data.
Business Continuity is maintained by addressing application risks to prevent operational disruptions due to software failures or cyber-attacks. This ensures consistent service delivery and business operations without unexpected downtime.
Regulatory Compliance is delivered through ARM, avoiding legal penalties and compliance by ensuring that applications meet key industry regulations and standards.
Reputation Management is important. By proactively managing risk, an organization reduces its chances of security incidents that can damage its reputation. Maintaining a secure and reliable application environment builds trust with customers, partners, and stakeholders.
Cost Savings through the avoidance of financial costs associated with incident response, remediation, legal fees, and potential fines can be achieved through the prevention of security incidents and operational failures.
Improved User Confidence is achieved with secure and reliable applications, leading to increased user satisfaction, loyalty, and potentially higher user retention and growth.
Risk Awareness and Mitigation is delivered through a structured approach to understanding and addressing potential risks, leading to better risk awareness and proactive mitigation strategies across the organization.
Efficient Resource Utilization is delivered through proper risk management, which ensures optimal resource use, focuses efforts on the most critical areas, and reduces time and money spent on reactive problem-solving.
Competitive Advantage in the market can be achieved if an organization can demonstrate its commitment to security and reliability.
Investor Confidence is improved when an organization can demonstrate robust ARM practices to actively manage potential risks, ensuring long-term stability and growth.
In summary, focusing on ARM enhances security, operational resilience, legal compliance, and customer trust while driving cost efficiencies and maintaining a competitive edge in the marketplace.
Important Questions Answered Using Application Risk Management
In addition to bringing real value to an organization, ARM addresses a range of critical questions to ensure applications' security, functionality, and compliance. Key questions answered using ARM include:
- What are the potential threats?
- What vulnerabilities exist within the application?
- What are the impacts of potential security incidents?
- How can risks be mitigated?
- Are the applications compliant with industry regulations and standards?
- What is the likelihood of a risk occurring?
- What is the state of the current security posture?
- How will security incidents be managed and responded to?
- What resources are needed to manage risks effectively?
- How do changes to the application affect risk levels?
- What are the roles and responsibilities in risk management?
- How are risks communicated and reported?
By addressing these questions, Application Risk Management ensures a proactive approach to identifying, assessing, and mitigating risks, ultimately supporting an organization's application security, reliability, and compliance.
Roles and Components of Risk Roles
To develop an effective and robust ARM framework, key roles across the business must be involved in the process. These include:
Risk Owners who are accountable for specific risks within their business units, implementing mitigation strategies and monitoring risk levels.
Risk Managers oversee the risk management process, coordinating among stakeholders and ensuring risks are properly managed.
Security Analysts conduct risk assessments, identify vulnerabilities, and recommend mitigation actions.
Developers implement secure coding practices and address identified vulnerabilities during application development.
Enterprise Architects integrate risk management principles into the IT architecture, ensuring robust structural security.
Compliance Officers ensure that applications comply with regulatory requirements and internal policies.
Executive Leadership provides strategic direction, oversight, and resource allocation for ARM efforts.
These roles will give an organization the necessary “task force” to develop ARM and combat adverse risks.
Risk Categories
The Institute of Risk Management (IRM) categorizes risk to provide a structured framework for identifying, analyzing, and managing risks across various domains. The key categorization components and types of risk as defined by IRM are:
Strategic Risks are risks that affect the organization's long-term goals and overall direction. Examples include market changes, competitive landscape shifts, mergers and acquisitions, regulatory changes, and technological innovations.
Operational Risks arise from day-to-day operations and affect the organization's ability to deliver products or services. Examples include process failures, supply chain disruptions, human errors, IT system failures, and health and safety incidents.
Financial Risks relate to financial performance and can affect an organization's profitability and financial stability. Examples include market risks (e.g., interest rates, exchange rates), credit, liquidity, and funding risks.
Compliance Risks are associated with failure to comply with laws, regulations, and industry standards. Examples include regulatory fines, legal penalties, non-compliance with data protection laws (e.g., GDPR), and corporate governance breaches.
Reputational Risks that affect the organization's reputation and stakeholder trust.
Examples include negative publicity, customer dissatisfaction, ethical breaches, and social responsibility failures.
Environmental Risks related to environmental factors and sustainability. Examples include natural disasters, climate change impacts, environmental regulations, and pollution liabilities.
Technology Risks arise from the use of technology within the organization. Examples include cybersecurity threats, data breaches, technological obsolescence, and software failures.
What Is an Application Security Risk Assessment?
An Application Security Risk Assessment (ASRA) systematically identifies, evaluates, and addresses application security risks. These application security assessments ensure that vulnerabilities and threats to an application are recognized and mitigated before they can be exploited to cause harm. Key aspects of an ASRA include:
-
Identification of assets to determine which application components (data, modules, interfaces, etc.) are critical and need protection.
-
Threat modeling to identify potential threats and attack vectors that could exploit vulnerabilities in the application.
-
Vulnerability analysis by examining the application for security weaknesses or flaws that threats could exploit. This often involves code reviews, security testing (e.g., static and dynamic analysis), and penetration testing.
-
Risk evaluation assesses the likelihood and potential impact of each identified threat and vulnerability. This helps prioritize which risks need immediate attention based on severity.
-
Mitigation strategies develop and implement measures to mitigate identified risks. This may involve patching vulnerabilities, strengthening authentication and authorization controls, improving encryption, and ensuring secure coding practices.
-
Documentation and reporting to record the assessment findings, including identified risks, their potential impacts, and the steps to mitigate them. Reporting these findings to relevant stakeholders ensures everyone knows the current security posture.
-
Compliance checks ensure that the application adheres to applicable legal and regulatory requirements.
-
Continuous monitoring and review establish ongoing monitoring to detect new risks as the application evolves and conduct periodic reviews to reassess and update the risk profile.
An ASRA is crucial for maintaining the security and integrity of software applications. It helps organizations proactively identify and mitigate risks, protect sensitive data and intellectual property, comply with regulations, and maintain trust with users and stakeholders.
Phases of Application Risk Management: The 9-Step Guide to Building a Comprehensive Program
To build a broad ARM program, it is important to complete several key initiatives. These will provide structure and consistency when developing an ARM program:
-
Define Objectives to establish clear ARM goals aligned with business objectives and regulatory requirements.
-
Stakeholder Engagement identifies and involves key stakeholders from IT, security, legal, and business units for collaborative efforts.
-
Resource Allocation secures necessary resources, including budget, tools, and skilled personnel to support the program.
-
Risk Identification creates a detailed inventory of applications, identifies potential threats, and assesses vulnerabilities using tools like static and dynamic analysis.
-
Risk Assessment analyzes risks regarding likelihood and impact, and prioritizes them based on severity to focus mitigation efforts.
-
Risk Mitigation develops and implements strategies to reduce risks, including applying patches, enhancing security controls, and integrating secure coding practices.
-
Training and Awareness for staff through campaigns to ensure understanding and compliance with security protocols.
-
Continuous Monitoring and periodic reviews to detect emerging threats and reassess risks.
-
Reporting and Continuous Improvement documents and communicates risk assessments and mitigation efforts, tracks key performance indicators (KPIs), conducts regular audits, and adapts the program based on feedback and evolving threats.
These steps ensure a comprehensive, proactive, and adaptive approach to managing application risks effectively.
/Illustrations/Basic%20steps%20in%20IT%20Risk%20Management_LP.png?width=300&height=266&name=Basic%20steps%20in%20IT%20Risk%20Management_LP.png)
Best Practices for Implementing Application Risk Management With EA
Implementing Application Risk Management within Enterprise Architecture involves integrating security principles into the EA framework to ensure applications are secure, reliable, and compliant. Key best practices for doing this include:
-
Align with business objectives to prioritize and address the most critical risks.
-
Integrate security by embedding security guidelines, standards, and policies within the EA framework to govern application development and deployment.
-
Adopt a risk-based approach by identifying, evaluating, and prioritizing risks based on their potential impact and likelihood using established risk assessment methodologies.
-
Collaborate across teams to address security considerations throughout the application lifecycle.
-
Develop threat models for critical applications to identify potential attack vectors and vulnerabilities.
-
Implement secure development practices, such as secure coding practices, conducting regular code reviews, and using automated tools for static and dynamic code analysis.
-
Utilize security frameworks and standards such as NIST, ISO/IEC 27001, and OWASP, to guide ARM implementation.
-
Continuous monitoring and improvement will detect new risks and ARM practices to adapt to evolving threats.
-
Define roles and responsibilities for risk management activities within the EA team and across the organization.
-
Conduct regular assessments and audits, including security assessments, vulnerability scans, penetration tests, and internal and external audits to ensure ARM effectiveness.
-
Maintain documentation and training for risk assessments, strategies, and controls, and provide ongoing training and awareness programs for relevant stakeholders.
-
Establish incident response plans and integrate them within the EA framework for coordinated responses.
-
Leverage automation tools: These enhance efficiency in vulnerability management, threat detection, and compliance monitoring.
-
Manage third-party risks to ensure they comply with security standards.
By following these best practices, organizations can effectively implement ARM within EA, ensuring comprehensive security and alignment with business objectives.
Application Risk Management Challenges
Several challenges that can affect the successful and effective implementation of an ARM program should be considered and, where appropriate, addressed:
-
As the Complexity of Modern Applications grows, encompassing microservices, cloud integrations, and third-party components, identifying and managing risks is becoming increasingly difficult.
-
Rapid Development Cycles using Agile and DevOps methodologies can lead to insufficient focus on security, with vulnerabilities being introduced and overlooked.
-
Resource Limitations, such as a lack of skilled personnel, tools, or budget, can lead to ineffective risk assessments or the implementation of insufficient security measures.
-
The Evolving Threat Landscape makes it challenging to stay ahead. New vulnerabilities and attack vectors emerge faster than organizations can address them.
-
Integration with Existing Processes without disrupting operations can be difficult, necessitating careful planning and coordination.
-
Compliance Requirements require continuous monitoring and adjustments to the ARM processes to ensure continued compliance.
-
Data Privacy and Protection of sensitive data across various application environments, including cloud, on-premises, and hybrid setups, adds complexity to application security risk management efforts.
-
Stakeholder Buy-in is essential but challenging due to differing priorities and understanding of ARM's importance.
-
Legacy Systems may lack modern security features, making them more vulnerable and challenging to protect without significant overhauls.
-
Tool Integration can be technically complex and resource-intensive when undertaking a thorough risk assessment.
These challenges necessitate a strategic, well-resourced approach to ARM, emphasizing proactive measures, continuous monitoring, and cross-functional collaboration.
Enterprise Application Risk Management With Ardoq: Secure What Matters Most to a Business
Application Risk Management using Ardoq focuses on securing critical business applications and data by providing a comprehensive, integrated approach to identifying, assessing, and mitigating risks. Ardoq offers several features that enhance risk management efforts:
-
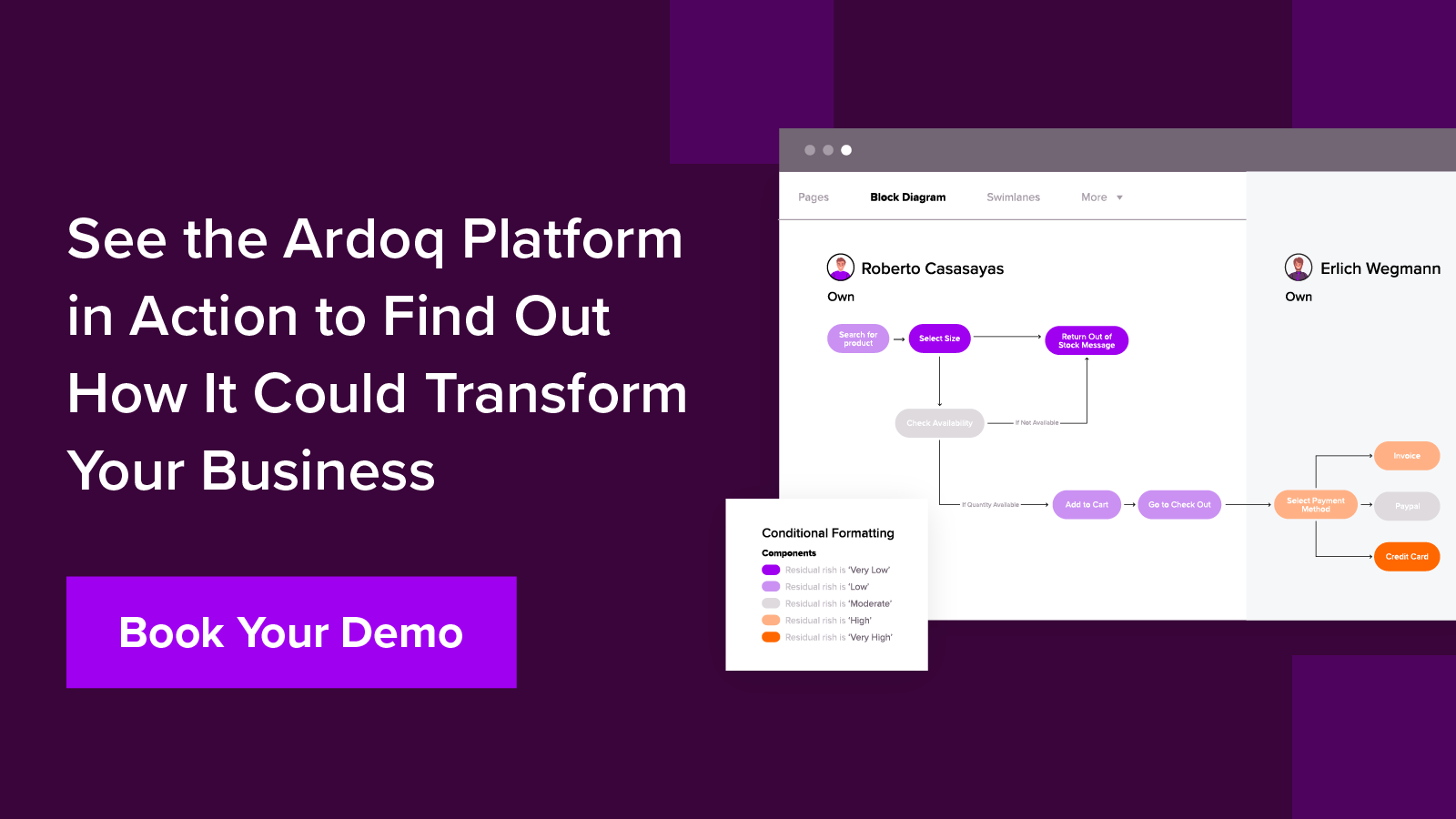
Centralized Documentation and Visualization allow organizations to document and visualize their entire application landscape in a centralized platform. This holistic view helps identify interdependencies and potential risks across applications, data flows, and infrastructure.
-
Dynamic Modeling and Mapping to create detailed maps and diagrams of applications, processes, and data flows. These visual representations help understand the architecture and pinpoint areas with potential vulnerabilities.
-
Real-Time Analytics and Insights provide views into the state of applications and their associated risks, enabling organizations to make informed decisions and prioritize risk mitigation efforts based on real-time data.
-
Impact Analysis to understand the potential effects of risks on critical business operations. This helps with evaluating risk severity and implementing appropriate mitigation strategies.
-
Scenario Planning to simulate different risk scenarios and assess the impact of various mitigation strategies. This proactive approach allows organizations to prepare for potential threats and minimize their impact.
-
Collaboration and Stakeholder Engagement are facilitated across different teams and stakeholders by providing a shared platform with real-time updates and notifications. This ensures that security considerations are communicated and addressed throughout the organization.
-
Compliance and Governance are supported by tools for documenting policies, standards, and controls. This simplifies ensuring that applications adhere to relevant laws and regulations.
-
Integration with Other Tools allows it to work seamlessly with other security and risk management tools. This ensures a cohesive approach to Enterprise App Risk Management, leveraging the strengths of multiple tools.
-
Automated Risk Assessments can be implemented to consistently evaluate applications against defined criteria, identify vulnerabilities, and prioritize risks effectively.
-
Continuous Monitoring and Reporting of the application landscape, with automated alerts and reporting features, ensures new risks are identified and addressed, maintaining an up-to-date risk profile.
By leveraging Ardoq’s Application Risk Management solution, businesses can secure their most critical assets, maintain compliance with regulatory requirements, and ensure the stability and security of their application environment. This extensive approach helps organizations mitigate risks proactively and protect what matters most to their business operations.
Get in touch to find out how Ardoq can help your organization with managing application risk and compliance more effectively.
FAQs About Application Risk Management
How Do Application Risk Assessments Work?
Application risk assessments systematically identify, evaluate, and mitigate security risks within software applications.
The process starts by cataloging application assets and potential threats, followed by vulnerability scanning through static and dynamic analysis. Identified risks are then analyzed in terms of likelihood and impact, enabling prioritization.
Mitigation strategies are formulated to address the most critical risks, such as applying security patches or enhancing access controls. Continuous monitoring ensures ongoing risk identification and management.
Regular reporting and compliance checks maintain adherence to regulatory standards.
This holistic approach ensures applications are secure, reliable, and aligned with organizational objectives.
How Do You Perform Application Risk Management?
Performing ARM requires a structured approach comprising:
-
Identify Assets and Threats to catalog all application components and identify potential threats.
-
Conduct Vulnerability Assessments using static and dynamic code analysis tools to detect security flaws.
-
Risk Evaluation assesses the likelihood and impact of identified risks.
-
Prioritize Risks based on severity to focus on the most critical issues first.
-
Mitigate Risks and implement appropriate measures such as patching, security controls, and secure coding practices.
-
Continuous Monitoring employs ongoing monitoring to detect new threats.
-
Training and Awareness to educate staff on best security practices.
-
Reporting and Compliance to document findings and ensure applications meet regulatory standards.
This structured process ensures effective risk management and application security.
 Ardoq
This article is written by Ardoq as it has multiple contributors, including subject matter experts.
Ardoq
This article is written by Ardoq as it has multiple contributors, including subject matter experts.