Welcome to October, Cybersecurity Awareness Month!
We’re doing our part for #BeCyberSmart by focusing on the risk management area of cybersecurity in a three-part blog series focusing on Enterprise Architecture and Cybersecurity Teams.
Where are you in the tangle of trying to open up communications between your Enterprise Architecture (EA) Team and the Cybersecurity Risk Management Team?
Some teams never get past the tangle or don’t know where to start. At worst, you’ve become just another statistic on the ever-growing list of publicly visible data breaches. In fact, data breaches might be the worry that keeps you up at night, wondering if you’ve done enough to ensure you’re not the next headline. At best, you’ve taken steps to build a common platform that non-technical people can understand.
Unfortunately, we all tend to believe our department is the most important, and this self-focus creates space for miscommunication between platform players. You’re probably living through this right now: the business team is focusing on how to grow more value at a faster rate, while the security team works to minimize the risk of cybersecurity breaches. Meanwhile, the Enterprise Architects (EAs) are thinking it would be so much better if everyone spoke the same language and considered the principles of Enterprise Security Architecture.
Sometimes, it may seem that all these teams don’t have a common understanding of risk and cybersecurity, although they are all trying to solve problems and drive the business in the same direction. However, each team understands the warnings in headline news. For example, 2021 saw the highest average cost of data breaches: data breach costs rose from USD 3.86 million to USD 4.24 million, the highest average in the last 17 years.
Digital Twin of an Organization, Security, and Risk Mitigation
Clear and open communication about security and risk can be challenging because the messages change as the enterprise innovates and adapts. While notifications and emails may not make an impression, a picture is worth more than a thousand words when it gets the message across. Two tools can produce these pictures and cut down on the words you need.
The Digital Twin of an Organization (DTO) gives you a virtual representation of your organization, showing how the company performs as a system. It’s also a highly effective communication tool. With it, you’re able to visualize ongoing projects and see where they overlap. In addition, it tracks processes, systems, and information.
The DTO modeling can be expanded with Scenarios. Using Scenarios, you can focus on various points to map out potential futures, including risk scenarios. From a risk management and security perspective, you can see what would happen if a critical system went down, which departments would be paralyzed, and how they could continue to function. For example, when mapping out the cybersecurity risk of ransomware hits, the Digital Twin of an Organization could give you a clear overview of which parts of the organization are most exposed and show how the attack could develop. Let’s say there’s a new virus affecting laptops that aren't fully patched. You can easily identify which parts have the most unpatched laptops. Then, you can focus your risk remediation effort towards those parts of the organization.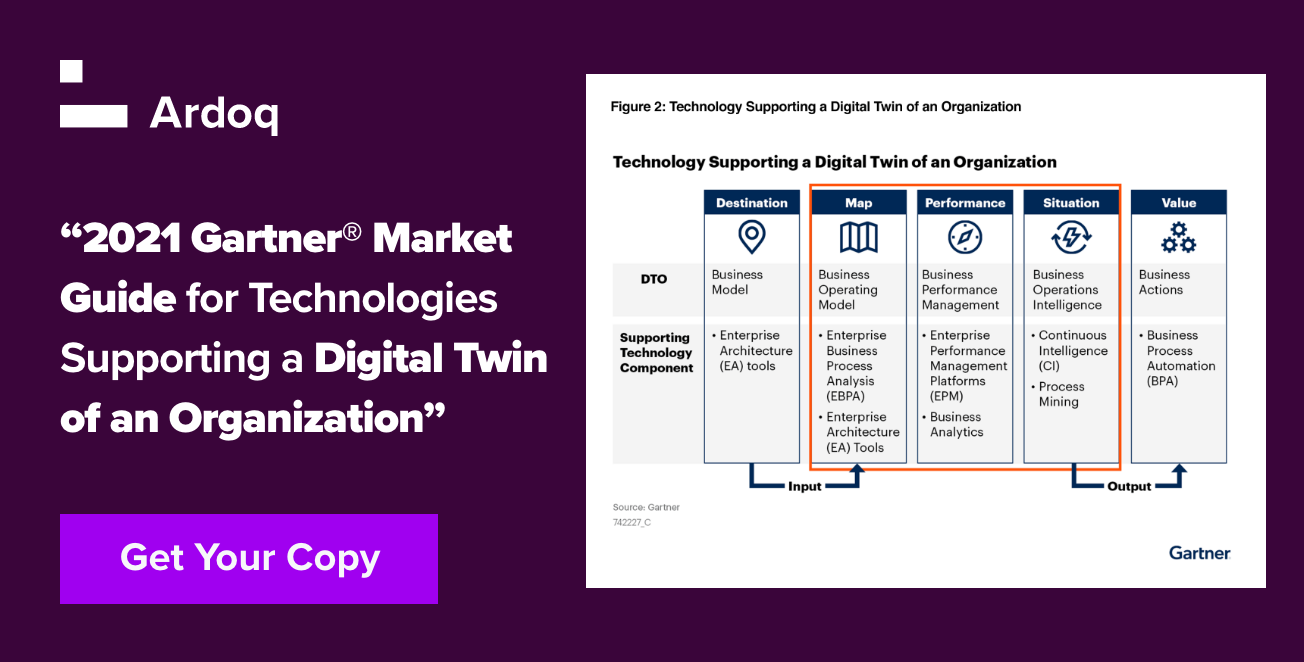
Following Data Flow
Understanding data flow helps you know what’s under the hood of the business and isolate weak points by presenting or showing which processes rely on which systems and where the data flows. For example, if your competition is Cloud-native and you're still struggling to set up VPN access to your on-premise IT infrastructure, that's not technical debt; that’s organizational debt. Cloud migration brings another risk into the picture. With cloud migration, you're moving critical business processes away from systems that may only be internally accessible to externally hosted (and accessible) modern solutions. Not only does everyone have to learn how to use new systems, but you also need to learn how to secure your cloud systems. This is a very different concept from how you secure your on-site IT systems.
Turning Cybersecurity Risk Management Malfunction into Cross-Function
Unpicking the communication knot starts with getting everyone to speak a common language. When everyone uses the same dictionary, you can calculate and communicate risk, show data flow, and model the hypothetical future impact of risk with the Digital Twin of an Organization. With the data, Enterprise Architects, security, and risk teams have the tools needed to show stakeholders the ‘why’ and have them listen to your message. When key stakeholders start to listen, these teams can become trusted advisors instead of unwanted nay-sayers.
🛡Want to learn how we optimize our customer's security assurance processes? ➡️ Read all about our SOC 2 attestation.
Disclaimer
1. Gartner, Market Guide for Technologies Supporting a Digital Twin of an Organization, Marc Kerremans, Tushar Srivastava, 13 July 2021.
2. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
3. Gartner® is a registered trademark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
4. This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Ardoq.
 Nick Murison
Nick Murison is Ardoq’s Chief Information Security Officer. He is passionate about helping Ardoq to meet our customers’ needs - safely and securely.
Nick Murison
Nick Murison is Ardoq’s Chief Information Security Officer. He is passionate about helping Ardoq to meet our customers’ needs - safely and securely.



.png?width=3000&name=ardoq-content-SecurityMonth(2).png)



